マネキャッシュの概要
マネキャッシュは、すべて自社グループで開発したManekash Online Casinoでしか遊べないオリジナルのスロットゲームを提供する新しいオンラインカジノです。マネキャッシュは、2020年の経験とライセンスを持つイギリスの大手ゲーム会社が開発しています。また、ジャックポットで巨額の賞金を獲得することも期待できます。今まで誰も回したことのないオリジナルのスロットを回すことができます。日本人向けに開発されたオンラインスロットの最大の特徴は、3×3リールのものが多いことで、パチンコ・パチスロファンの方にもきっとご満足いただけると思います。その上、マネキャッシュで正々堂々の10ドル入金不要ボーナスがありますので、試してみても損がないでしょう!?
マネキャッシュの評判と信頼性
マネキャッシュの評判は主に良いといえます。若いオンカジですが、マネキャッシュは詐欺ではありません。マネキャッシュが提供するゲームは、第三者によって監査・認証された乱数発生器を使用しているため、詐欺行為のリスクはありません。また、プレイヤーが安心して入金・出金できるように、厳選された信頼性の高い支払い方法のみを提供しています。もちろん、マネキャッシュは違法ではありません。このオンラインカジノを運営するIntouch Games Ltdは、キュラソー島で発行されたライセンスを保有し、合法的にオンカジを運営しています。
マネキャッシュの良い評判

マネキャッシュって、若いオンカジですけど、大丈夫ですか。評判はどうですか?

大丈夫です!あれこれの口コミを見てみましょう!
独占スロットが面白い
マネキャッシュの良い評判をもたらすものは、もちろん「Slot Factory」の独占スロットです。全て自社開発で、日本初のスロットですので、他にはない革新的なゲームをお求めの方にお勧めです。ほとんどのスロットがシンプルなルールなので、初心者の方でも問題なく楽しめるという評判を持っています。スロットの総数は約50種類と少ないですが、今後も続々と新しいスロットを追加していく予定だそうです。

また、ほぼすべてのスロットにプログレッシブ・ジャックポットが搭載されているので、大当たりの可能性があちこちにあるのも魅力です。特に人気の高いゲームの中には、最大20万ドル(約2000万円❣❣❣)のジャックポットもあります。
ボーナスが多い
マネキャッシュでは、10ドルの入金不要ボーナス(無料ボーナス、登録ボーナスともいう)、最初の4回の入金で1000ドルのボーナス、100回のフリースピンなど、登録ボーナスも充実しています。賭け条件が20倍に設定されているのも嬉しいポイントです。
マネキャッシュの良くない評判
出金時間が遅い
出金が遅くなる場合があります。公式サイトでは「1営業日」と記載されていますが、数日遅れることもあるようです。本人確認ができない場合、出金が遅れることがあると言われています。
大人気なスロットがない
マネキャッシュでは、Play’n’Go、NetEnt、Yggdrasil、Microgamingなどのような有名なプロバイダーのスロットゲームを提供していないので、他のゲームをプレイすることはできない。
マネキャッシュの口コミ
ツイッターとりでは自社開発のスロットを賞賛するコメントが多く見受けられました。マネキャッシュならではのスロットに魅力を感じるプレイヤーもいるようです。また、自社開発のスロットのユニークなデザインがクセになるというコメントもありました。入金不要ボーナスをちゃんと獲得できるというコメントも多いですね!
マネキャッシュの登録方法

マネキャッシュで登録したら携帯電話番号が必要ですか?

はい、SMSで確認が必要です!
マネキャッシュの登録方法はけっこう簡単です。画面上部にある「今すぐ登録」ボタンをタップします。すると、以下のようなアカウント情報の登録画面が表示されます。
最初に入力する情報は以下の通りです。
- ユーザー名
- 携帯電話番号
- Eメールアドレス
- パスワード
- パスワード(確認)
ユーザー名は5文字以上16文字以下、パスワードは6文字以上16文字以下で入力してください。使用できる文字は、半角英数文字と5種類の特殊文字(@. &%$)です。また、キャリアのメールアドレスを使用することもできますが、メールアドレスの変更が面倒なので、フリーのメールアドレスやPC用のメールアドレスを使用することをお勧めします。すべての情報を入力したら、「続ける」をタップします。
続いて、以下の情報を入力します(マネキャッシュの本人確認に役に立ちます)。
- 名字(日本語)
- 名前(日本語)
- 生年月日
- 都道府県。市、区、町、村
- 住所(町名以下) 日本語で入力することも可能です。
すべての項目を入力したら、「私は18歳以上で、マネカセの利用規約に同意します」にチェックを入れてください。アカウント登録時のトラブルを防ぐため、必ず利用規約をよくお読みください。その後、ロボットではないことをグーグルさんに確認し、グーグルのキャプチャーに合格しなければなりません。
マネキャッシュに登録した電話番号にSMSが届きましたら、「アクティベーションコード」を入力して「今すぐアクティベート」をタップしてください。SMSが届かない場合は、「再送」をタップしてください。確認用のアクティベーションコードを正しく入力すると、マネキャッシュの登録が完了します。
マネキャッシュのボーナス
マネキャッシュはボーナスがたっぷりです!なんと6種類があります!キャンペーン中に様々なボーナスも獲得できます。そしてボーナスの賭け条件はいつも20倍だけですから、満たしやすいで安心してボーナスをゲット!
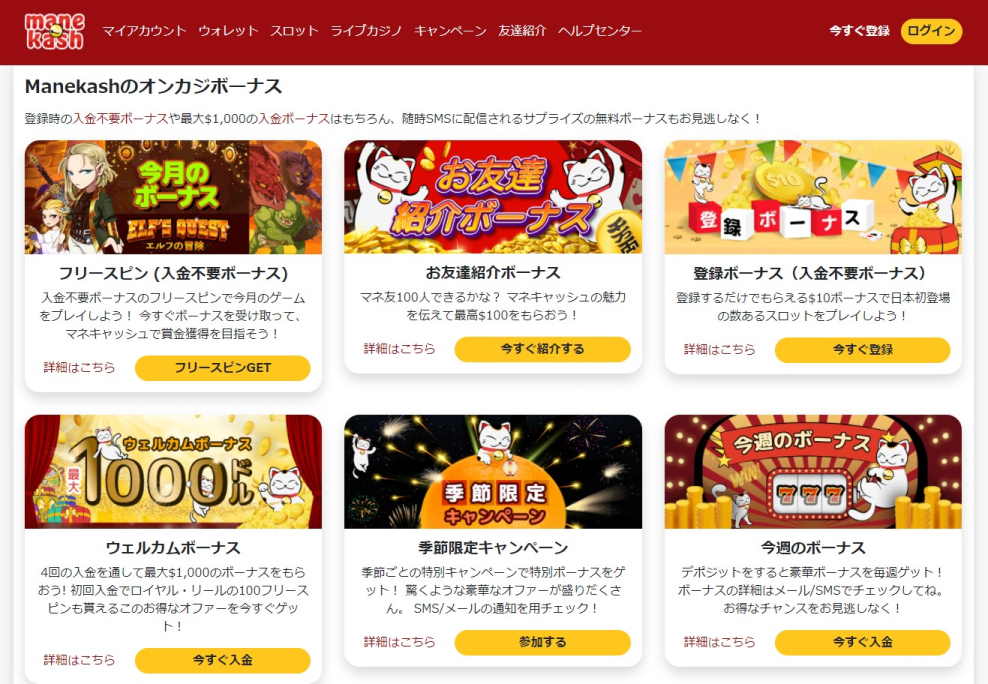
マネキャッシュの入金不要ボーナス
登録するだけでもらえる10ドルの入金不要ボーナスがあります。このボーナスは、お客様が登録してアカウントを有効にすると、自動的に与えられます。マネキャッシュの入金不要ボーナスの条件は以下の通りです。
- 賭け条件(出金条件)は20倍
- 有効期限は登録から7日間
- 最低出金額は50ドル、最高出金額は100ドル
マネキャッシュのお友達紹介ボーナス
マネキャッシュのことを伝えて、最大100ドルをゲットしましょう!お友達は、紹介用のSMSまたはEメールを受け取ってから3日以内に、紹介用のリンクからアカウント登録を完了する必要があります。ご紹介いただいたお友達には、初回入金完了時に、最大200ドルの100%入金ボーナスと100回のフリースピンを差し上げます。
マネキャッシュの入金ボーナス(リロードボーナス)
1回目から4回目までの入金でもらえる合計1,000ドルの登録ボーナスをご用意しています。さらに、初回入金時には、合計100回のフリースピンも獲得できます。
- 初回入金 最高$200の100%ボーナス?Reel Royalty ロイヤル・リールという独占スロットで遊べるフリースピン100回分
- 2回目入金 最高$250の50%ボーナス
- 3回目入金 最高$250の100%ボーナス
- 4回目入金 最高$300の50%ボーナス
マネキャッシュの入金ボーナスはそれぞれ$10以上入金することで、自動的にアカウントに進呈されます。
- 賭け条件は20倍
- 有効期限は30日間
マネキャッシュのフリースピンボーナス
10ドル以上の初回入金で合計100回のフリースピンを獲得できます。フリースピンは、10日間毎日10回付与されます。このフリースピンは Reel Royalty ロイヤル・リール で利用できます。賭け条件は、通常のボーナスと同じ20倍です。
マネキャッシュの季節限定キャンペーン
シーズンごとの特別キャンペーン?でボーナスをゲットしよう! SMS/Eメールの通知をチェックして、素晴らしいオファーを手に入れましょう。
マネキャッシュの毎週ボーナスキャンペーン
入金すると、毎週大きなボーナスがもらえます! ボーナスの詳細については、Eメール/SMSをご確認ください。お得なチャンスをお見逃しなく!
マネキャッシュの賭け条件
マネキャッシュボーナスには、けっこう優しい20倍の賭け条件がついています。この賭け条件を満たした場合、賞金はお客様のキャッシュアカウントに反映されます。
マネキャッシュのVIPプログラム
マネキャッシュは現在、VIPプログラムやロイヤルティプログラムを持っていませんが、将来的には導入を検討しています。
マネキャッシュの入金方法、入金限度額、入金手数料、入金時間

決まった!マネキャッシュで入金したい!どんな入金方法がマシ?

クレジットカードでマネキャッシュで入金してみよう!
入金不要ボーナスはデモプレイの感じがするでしょうwww実際のギャンブルの魅力が感じられるように現金でプレイしてみましょう!マネキャッシュは、3種類のクレジットカード、銀行送金、仮想通貨(ビットコイン)、エコペイズ、ヴィーナスポイントに対応しています。
- クレジットカード:JCBカード、マスターカード(Master Card)、ビザカード(Visa)、Diners Club International
- 電子経済サービス:エコペイズ(Ecopayz)、ヴィーナスポイント(Venus Point)
- 仮想通貨:Bitcoin(ビットコイン)
- 銀行送金
| 入金方法 | 入金手数料 | 入金限度額 | 入金時間 |
| クレジットカード (VISA・MasterCard・JCB) | 無料 | 10〜2000ドル | 1日間 |
| ヴィーナスポイント | 無料 | 10~2000ドル | 1日間 |
| エコペイズ | 無料 | 5~5000ドル | 1日間 |
| ビットコイン | 無料 | 10~20000ドル | 1日間 |
| 銀行振込 | 無料 | 10~2000ドル | 銀行営業時間内 |

マネキャッシュの手数料はどうなるけど、、、

安心してください!マネキャッシュの入金・出金手数料は全て無料です!
マネキャッシュの入金方法は以下の通りです。入金するには、「ウォレット」→「入金」と進み、支払い方法を選択し、入金額と必要な情報を入力します。

マネキャッシュクレジットカード(Visa、MasterCard、JCB)でのご入金方法について
- 表示された入金方法のリストから「クレジットカード」を選択します。
- 入金したい金額を入力します。入金」ボタンをクリックします。
- カード番号、カード有効期限、CVV番号(カード裏面に記載されている3桁の数字)、カード所有者を入力します。これらの情報をすべて入力したら、「購入」をクリックします。これで入金処理が完了します。
入金制限などの自主規制ツールは、現時点では利用できませんが、将来的には導入する予定です。

なぜマネキャッシュで入金できないかなあ、、、

本人確認をちゃんとしましたか?
マネキャッシュで入金できない理由はいくつかありますが、多くの場合、以下のような理由が考えられます。
- 本人確認の失敗
- 入金決済サービスの停止
- インターネット接続の不具合
入金決済サービスが停止した場合、エラーメッセージが表示されます。この場合は、ライブチャットまたは [email protected] までカスタマーサポートにご連絡ください。
マネキャッシュの出金方法、出金限度額、出金手数料、出勤時間

マネキャッシュの出金方法、どちらがオススメできますか?

エコペイズで出金がオススメです!
マネキャッシュで出金すると、「ウォレット」>「出金」からお支払い方法を選択して行います。最初の出金の際にアカウントの確認が必要です。アカウントの確認は、以下の必要書類を提出することで行われます。クレジットカードでご入金された場合は、クレジットカードの証明書も必要となります。
マネキャッシュで以降の出金方法が可能です。
- エコペイズ(Ecopayz)
- ヴィーナスポイント(Venus Point)
- ビットコイン(Bitcoin)
| 出金方法 | 出金手数料 | 出金限度額 | 出金時間 |
| ヴィーナスポイント | 無料 | 20~500ドル | 一日間 |
| エコペイズ | 無料 | 50~500ドル | 一日間 |
| ビットコイン | 無料 | 50~500ドル | 一日間 |
マネキャッシュで出金するためにに一番便利なのは、電信送金サービスのEcopays(エコペイズ)です。入金にも出金にもとても便利です。出金する前に、ボーナスやフリースピンが消えてしまうという警告メッセージが表示されますが、問題なければ出金依頼をすることができます。別枠のボーナスは、現金で勝ったらすぐに出金できます。

マネキャッシュから出金が来ないですけど、、、

そうですね、出金が遅れる場合もありますね。
マネキャッシュで出金できない場合もありますが、マネキャッシュは良い評判を持つオンラインカジノですので、安心してください!一般的に、ボーナス(フリースピンを含む)で発生した賞金は、すぐには出金せず、出金までに一定のプレイ回数が必要となります。これを「ボーナス賭け条件」といいます。マネキャッシュのボーナス賭け条件は20倍に設定されています。
例えば、登録時に受け取った$10の無料ボーナスには20倍のボーナス賭け条件が設定されていますので、$10の無料ボーナスを出金するには、$200($10 x 20 = $200)分のプレイが必要となります。もちろん、入金不要ボーナスをただで出金できない!www
入金額は1倍の賭け条件を満たせば出金可能
マネキャッシュに入金したリアルマネーを出金したい場合は、入金額と同じかそれ以上の金額を賭けることで出金できます。例えば、100ドルを入金した場合、合計100ドル分の賭けをすることで出金できます。賭け条件消化の概念はリアルマネーには適用されませんので、ライブゲームのみをプレイすることができます。他のオンラインカジノでは、1xよりも厳しい賭け条件が設定されていることがよくあります。
エコペイズによる出金する場合、入出金歴史が必要
マネキャッシュから資金を出金するためには、エコペイズから最低1回の入金が必要です。5ドルから入金できますので、できるだけ早く入金履歴を残しておきましょう。エコペイズにはクレジットカードによる課金オプションはありませんので、マネキャッシュへの入金には以下のいずれかの方法をご利用ください。
*現地入金(銀行送金)による入金
出金額上限は500ドル
オンラインカジノにクレジットカードで入金し、エコペイズ・ローダに出金する 一度に出金できる最大金額は500ドルのみです。?1回の出金上限額は500ドルです。一度に出金ごとに最大金額は500ドルです。もし1500ドルを出金したい場合は、3回に分けて取引を行う必要があります。
出金が遅くなる場合はある
前述の通り、マネキャッシュの出金スピードはかなり遅いので、多額の出金が完了するまでにはかなりの時間がかかることを覚悟しなければなりません。ハイローラーにとってはかなり使いづらいオンラインカジノと言えます。✖
本人確認が必要
口座確認書類は、「マイアカウント」>「口座確認」から画像をアップロードするか、Eメール([email protected])で画像を送信することで行います。電子メールで送信する場合は、登録した電話番号をメールの本文に記載する必要があります。
- 写真付きの身分証明書。運転免許証(両面)、パスポート(写真のあるページ)、マイナンバーカード(表面)など
- 住所確認書類。氏名、住所の確認は、3ヶ月以内に発行された住民票、公共料金の請求書など
- クレジットカード(両面):氏名、カード番号、有効期限、署名(3桁のCVVコード非表)
マネキャッシュのゲーム
マネキャッシュカジノは独占スロット専門店でと思われていますが、実はライブカジノも楽しめます!スポーツベットがまだないんですけど、ほぼほぼフールスタックなオンラインカジノです!

マネキャッシュのライブカジノ体験
マネキャッシュでは、Evolution社やEzugi社のゲームプロバイダーによる40種類以上のライブカジノゲームをプレイすることができます。ライブカジノゲームの魅力は、本物のカジノハウスの臨場感をオンラインで手軽に体験できることです。最高のライブカジノゲームを厳選し、おすすめゲームリストをご用意しました! 数あるライブカジノゲームの中でも特におすすめのゲームをご紹介します。9を狙う、アジアで最も人気のあるゲーム「バカラ」。ルーレット、ルーレットホイールの結果を予測するゲームです。人気のライブカジノゲームを集めた「トップカジノゲーム」、賑やかなトークショー「ゲームショー」、定番のポーカーゲーム「テキサスホールデム」なども要チェックです。各ライブカジノゲームの詳しいルールや操作方法は、各ゲームのページに掲載されています。
マネキャッシュのモバイルカジノとライブカジノ

通勤中でつまんないだから、スマホからオンカジで遊びたい!マネキャッシュってアプリがあるの?

マネキャッシュはアプリがないですけど、スマホから使えます!
マネキャッシュは、iPhone、Android、タブレットなどのモバイルデバイス(iOS 10またはAndroid 5.0以上)に対応しています。PC版と同様にスロットだけでなく、ライブカジノも楽しめます。現在アプリはありませんが、ホーム画面に追加することで、マネキャッシュのウェブサイトに簡単かつ迅速にアクセスすることができます。
マネキャッシュのゲームソフト
何はともあれ、マネキャッシュのスロットゲームは、同じ運営会社である「Slot Factory」というゲームプロバイダーのオリジナル作品です。特に人気があるのは、「クリスピー・キャッシュ」や「フルーツ・スロット・ミニ」など、パチスロ感覚で遊べるゲームです。

最も有名なSlot Factoryのスロットは
- Reel Royalty ロイヤル・リール (最大配当 $205,146.44)
- Fire and Gold 炎のドラゴン(最大配当 $165,901.16)
- Emerald rainbow wins エメラルドの虹 (最大配当 $159,821.06)
マネキャッシュの日本語カスタマーサポート

お困りですか?マネキャッシュで電話サポートがないですけど、ライブチャットやメールまでお気軽にお問い合わせください!
日本語ライブチャットは、下記時間で受け付けています。
- 夏季 月曜日 – 金曜日:15時から24時まで (日本時間)
- 冬季 月曜日 – 金曜日:16時から25時まで (日本時間)
ライブチャットが時間外の場合は、マネキャッシュのメールでお問い合わせください。
- お問い合わせ全般:[email protected]
- 書類ご送付用:[email protected]
- 個人情報の取り扱いに関するお問い合わせ:[email protected]
マネキャッシュはオススメ?あれこれの情報まとめ
マネキャッシュは、他のオンラインカジノとは一線を画す独自性を持ったオンラインカジノです。新しいオンラインカジノですけど、良い評判を持つマネキャッシュをプレイしても、昔のオンラインカジノと同じでつまらないと感じている人であれば、マネキャッシュは非常に魅力的なオンカジだと言えるでしょう。興味があったら、10ドルのマネキャッシュ 入金不要ボーナスを活用して試してみてください❣














